Telecom Security – Part 5 of 10 in the series.
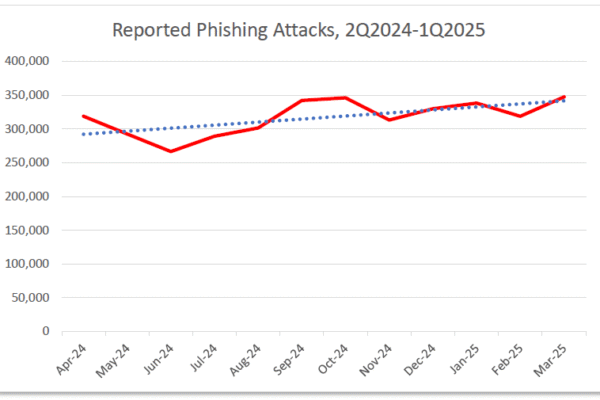
Social platforms now host a meaningful slice of global phishing activity – APWG counted ~1,003,924 unique phishing sites in Q1 2025, and the volume rose again in Q2! That’s millions of risky links surfacing every month, and a growing number of them are delivered through feeds, DMs, and bio links.
Phishing used to live mostly in messages and emails. Today, attackers treat social networks as first-class distribution channels: they post a short link in a Post, Story, DM an “urgent” notice, or hide a malicious landing behind a profile bio (Link-in-Bio). Researchers have observed campaigns that use legitimate platform redirects (TikTok, for example) as stealthy first hops to credential-phishing pages.
At the same time, defenders are losing advantage. Security tooling that checks only the visible domain or uses static blocklists misses multi-hop redirect chains and links that are dynamically generated or executed by JavaScript. Cloudflare’s recent research shows attackers abusing link-wrapping and redirect services to mask malicious payloads and evade detection, turning previously protective controls into attack vectors
Three technical and product weak points make social-platform phishing so effective:
Short links & link-in-bio aggregators
Shorteners and bio-link services collapse complex URLs into tiny tokens users trust, and they’re repeatedly abused to hide final destinations. Shortener operators run abuse programs, but detection is reactive by nature, meaning it only happens AFTER users are hurt.Open redirects and platform redirects
Legitimate redirect features (profile links, share UIs) can be abused as covert proxies that bounce victims through benign domains before landing on malicious pages. Cofense and others have documented TikTok/open-redirect abuse in credential attacks.Phishing-as-a-Service (PhaaS) & disposable domains
Attack kits spin up hundreds of throwaway domains and templates in hours; Microsoft and partners recently disrupted an operation that used hundreds of domains to steal thousands of credentials, demonstrating how quickly attackers can scale.
Because of these factors, surface-level scanning (check-first-hop, static lists) and slow manual review are insufficient — crowds and speed win for attackers.
Platforms must stop treating links as incidental UX items and start treating them as security objects. Practical, deployable capabilities:
Full redirect-chain resolution (in a real browser): Expand every shared URL (shorteners, bio links, platform redirects), execute JavaScript and follow meta-refresh so the canonical landing is revealed before the link is broadly visible.
Fast dynamic sandboxing of final landings: Short automated runs that detect credential forms, invisible iframes, unusual network calls or drive-by payloads — seconds, not hours.
Heuristic + reputation scoring of chains: features such as chain length, final-domain age, WHOIS privacy, hosting patterns and known PhaaS indicators create a reliable risk signal.
Behavioral signal fusion: correlate URL risk with account telemetry (DM/post velocity, newly created accounts posting links, geo/device anomalies) to spot compromised accounts and coordinated campaigns.
Graduated mitigation workflows: interstitial warnings for medium risk, automatic throttling + verification for high risk, and automated takedown requests for confirmed malicious infrastructure.
These are the exact capabilities that stop high-reach campaigns before they go viral — and they’re the core strengths you should expect from a world-class URL database and scanner.
Fortress Database and URL Scanner powers link security at scale. Here’s what it does best:
Real-time chain resolution & canonicalization
Expand every shared URL in a real browser (execute JS, follow meta-refresh) and store the canonical final landing — so you block the destination, not the distracting first hop.Lightning-fast sandboxing & verdicts
Run short dynamic sandboxes and return low-latency decisions at scale, so you stop threats without breaking user experience.Hybrid risk engine + reputation graph
Combine ML, User+AI-Created Rules, and threat feeds with rich signals (domain age, registrar patterns, known PhaaS markers) to deliver one simple, actionable risk score.Signal fusion & open APIs
Fuse URL risk with account and traffic telemetry (DM/post velocity, geo/device anomalies) via easy APIs, so you spot compromised accounts and coordinated campaigns with high confidence.Automated remediation & takedown orchestration
Push IOCs automatically to shortener vendors, registrars and partners, trigger takedowns and remove reusable malicious infrastructure fast.Enterprise ops, low friction & compliance
Ship with dashboards, SOC hooks, allow-lists and governance controls, plus flexible deployment (cloud/on-prem/hybrid) and onboarding — built to minimize false positives and meet enterprise requirements.
Social-platform phishing is not an edge case — it’s a high-volume, high-trust attack surface. Platforms that expand, analyze and score links in real time – can stop the majority of viral phishing before it harms users or brands.
If you manage product or security for a social app, aggregator or CPaaS, start by treating every shared URL as a security event: expand it, sandbox it, score it, and automate remediation.
Or, just use Fortress DB & URL Scanner. Brilliantly complicated, beautifully simple.