Telecom Security – Part 6 of 10 in the series.
In messaging, more traffic doesn’t always mean more success.
Across today’s A2P ecosystem, billions of messages that appear legitimate are actually fake – generated by bots, scripts, or shady routing partners.
The industry calls it Artificially Inflated Traffic (AIT), or more bluntly, SMS pumping.
A2P SMS remains a trusted channel for authentication and alerts, yet fraudsters have found a way to turn that trust into a cash machine. One major social platform, Twitter (X), reportedly lost $60 million per year to inflated OTP messages. Multiply that across banks, delivery apps, and retailers, and the total damage easily reaches into the billions.
What Exactly Is AIT — and Why It’s So Hard to See
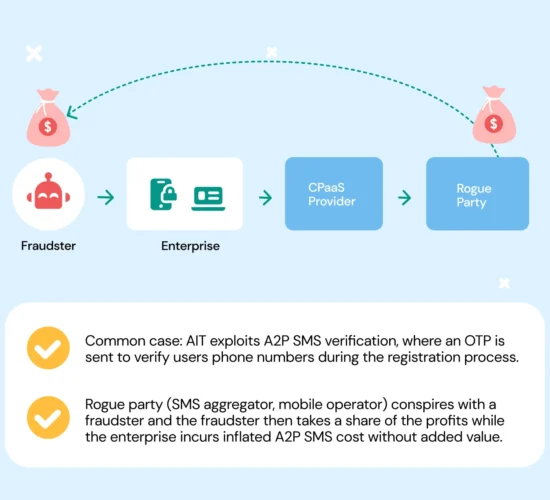
AIT attacks exploit automation.
Bots repeatedly trigger real SMS flows — for example, by filling out sign-up or password-reset forms. Each request sends an OTP to numbers controlled by the attackers.
Because the messages travel through normal routes and generate successful delivery receipts, nothing appears wrong. The enterprise pays for every message; the operator processes every one; the fraudster collects the profit.
According to Soprano Design, AIT often hides inside genuine traffic patterns: small volume bursts across diverse prefixes, realistic delivery ratios, and authentic sender IDs. Traditional filters can’t flag these anomalies fast enough — they look too normal.
The Real Damage – Revenue & Reputation
AIT drains budgets quietly.
Unexplained spikes on invoices, inflated KPIs, and confused support teams chasing “phantom” sign-ups are early warning signs.
Beyond the direct cost, there’s data pollution. Juniper Research notes that A2P traffic exceeded 2.7 trillion messages in 2023, projected to surpass 3.5 trillion by 2025 – a perfect hiding ground for inflated traffic. Even if only 2 percent is fraudulent, that’s billions of fake messages.
Operationally, AIT wastes bandwidth, skews analytics, and erodes customer trust. For operators and CPaaS providers, it threatens the credibility of SMS as a secure, reliable channel.
Ohad Kamer, CMO & Co-Founder of Atrinet, said:
“AIT is a silent killer of ROI in enterprise messaging.
It doesn’t attack users, it attacks your margins.”
How Fortress FW Outsmarts AIT
Defending against AIT isn’t just about blocking bad numbers;
It’s about seeing patterns, understanding intent, and reacting in real time.
Fortress can classify messages as OTP.
By distinguishing verification messages from Marketing or Alerts, Fortress FW can apply focused monitoring on traffic flows, sender behavior, and routing paths in real-time.
It sees the whole flow:
Sudden velocity spikes in OTP messages
Repeated requests from the same application IDs
Abnormal route changes or delivery-report loops
Geographic clusters that don’t match real user bases
Sinch notes that AIT attacks can raise traffic volumes by 10–20X within minutes, overwhelming traditional monitoring tools. Fortress FW’s machine learning engine detects those anomalies early by analyzing historical baselines, message velocity, and destination diversity.
Its AI behavioral engine continuously learns what “normal” traffic looks like for each client or tenant. When patterns deviate – whether by volume, timing, or distribution – Fortress FW flags, throttles, or blocks them instantly.
This isn’t static filtering. It’s adaptive defense: a system that evolves as fraud tactics evolve.
For decision makers, the value is clear:
Revenue protection: Stop paying for fake traffic before it’s billed.
Operational clarity: Clean, trustworthy analytics.
Customer trust: Real users, real conversions, zero disruption.
The combination of data depth, classification accuracy, and adaptive AI gives Fortress FW a clear advantage:
- Detects abnormal OTP or messaging traffic before it becomes a billing issue.
- Learns your network’s normal behavior to minimize disruption.
- Operates in real time, without adding latency or requiring routing changes.
- Provides transparent reports so fraud and finance teams can act with confidence.
The result is simple: no fake users, no wasted SMS spend, no erosion of trust.
Don’t Let AIT Eat Your Margins
AIT doesn’t steal passwords or data; it steals money, time, and trust.
The danger lies in its invisibility – by the time finance notices, the damage is already invoiced.
Fortress FW changes that.
By analyzing traffic behavior in real time and learning each network’s unique signature, it identifies and neutralizes inflated traffic before it reaches your bill or your brand.
“Fraudsters don’t need to break encryption;
They just need your system to keep sending.”
– Yoav Segman, Head of VAS & Security
With Fortress, they can’t.