Telecom Security – Part 4 of 10 in the series.
Communications Platform as a Service (CPaaS) providers like Twilio and Telnyx sit at the heart of enterprise messaging. Recently, regulators, courts, and customers have all sent a clear message: if malicious traffic slips through, the platform pays the price.
Recent headlines prove the stakes:
T-Mobile now enforces Severity-0 non-compliance fines for messaging violations like phishing, smishing, or social-engineering. Tier 1 violations can cost up to $2,000 per incident
In 2024, Twilio faced a TCPA class-action lawsuit over traffic enabled by its platform.
Carriers like T-Mobile enforce up to $10,000 fines per incident for phishing or smishing traffic.
Twilio confirmed an SMS phishing attack (smishing) where employees were tricked via fake IT messages, allowing attackers to access customer data.
These are not isolated cases. They’re signals that weak URL defenses are costing CPaaS platforms millions in fines, lawsuits, and customer churn.
Every CPaaS provider talks about “fraud detection,” but the truth is simple:
If the URL database behind your scanner is weak, everything else fails.
Most failures happen because databases:
Aren’t updated in real time.
Don’t use AI or ML to catch zero-day phishing domains.
Lack Google Web Risk integration, missing global threat visibility.
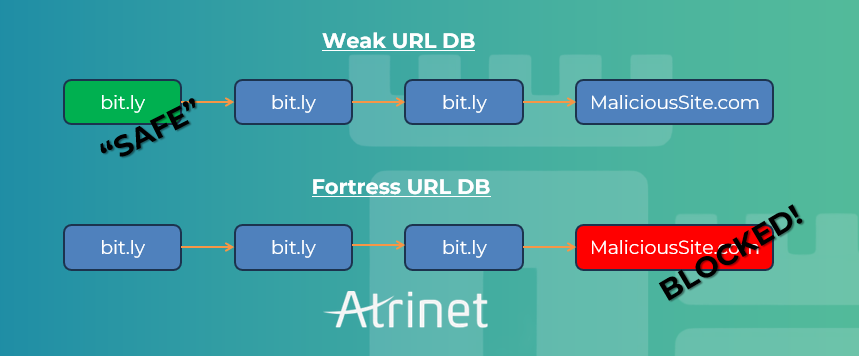
Worst of all, can’t scan shortened links like bit.ly, tinyurl, or t.co.
That last gap – shortened links – is the most dangerous. Attackers hide behind redirects to mask phishing domains. Without full expansion and analysis, a malicious link looks harmless until it’s too late. For CPaaS security, ignoring shortened links is like locking the front door but leaving the window wide open.
To protect platforms, enterprises, and end-users, the URL DB must evolve.
The gold standard for CPaaS security |& URL Scanners now includes:
Real-time updates – phishing domains emerge by the second.
AI + heuristics – catching obfuscation and zero-day phishing tricks.
Google Web Risk – leveraging one of the largest threat intelligence feeds in the world.
Ultra-low latency – sub-millisecond lookups to keep SMS and API traffic instant.
Shortened link resolution – expanding and inspecting every redirect chain to expose the true destination.
Without this, CPaaS providers will keep paying fines, losing customers, and seeing their brand names dragged into headlines.
This is exactly why we built Atrinet Fortress URL Scanner DB.
| Capability | Weak / Legacy URL DB | Atrinet Fortress DB |
|---|---|---|
| Database freshness | Updates slowly, missing new phishing domains | Real-time updates, catching threats as they emerge |
| AI/ML detection | Basic or rule-based only | AI + heuristics, detecting zero-day phishing patterns |
| Google Web Risk integration | Absent or partial | Full integration with Google Web Risk |
| Latency | High lookup delays, slows messaging | Ultra-low latency (<1 ms) for seamless traffic |
| Shortened link support | Cannot expand bit.ly, tinyurl, t.co or other redirects | Full shortened link scanning, resolving every redirect chain |
| Deployment flexibility | Cloud-only, limited integration | Cloud or on-prem, for best performance |
With Fortress DB, CPaaS providers don’t just check a compliance box – they eliminate the very vector attackers rely on most.
The message is clear: fines, lawsuits, and churn aren’t “possible.” They’re already happening.
The difference between CPaaS companies that thrive and those that fall behind will be the strength of their URL database. A DB that can’t handle shortened links or real-time threats is a liability.
Atrinet Fortress DB is the answer.
It’s real-time, AI-powered, Google Web Risk-integrated, and built to neutralize shortened links before they damage your platform, your customers, and your reputation.