Telecom Security – Part 2 of 10 in the series.
UPI Fraud (Unified Payments Interface) isn’t just big — it’s everywhere.
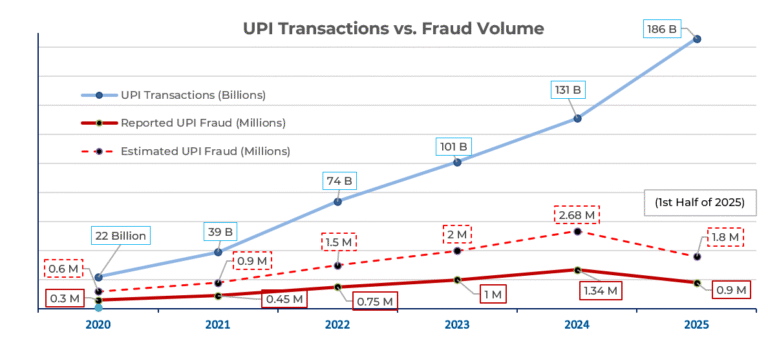
In FY25 alone, it processed over 185 billion transactions across 500 million users, connecting families, businesses, and services in real time.
But there’s a cost that’s not in the reports.
A 2025 survey found that 1 in 5 Indian families has already fallen victim to UPI fraud.
And 51% of them never told anyone.
This isn’t just a consumer problem.
It’s a blind spot — one that’s spreading across networks without being seen, logged, or stopped.
And when fraud moves in silence, it grows fast.
The result:
Malicious traffic rides freely over trusted infrastructure, often without the operator ever knowing.
It’s easy to talk about UPI Fraud in numbers. But here’s what it looks like up close:
Junagadh Vendor
A vegetable seller received a call from someone claiming to be a relative in a medical emergency. The caller knew personal information and sent him a malicious link.
He was convinced. He transferred ₹1.86 lakh (≈ $2,240) before realizing it was a scam.
Read the case – Times of IndiaElectricity App Scam
A man got an SMS warning of a power disconnection. The link led to what looked like a bill payment portal – clean, branded, familiar. In minutes, ₹91,000 (≈ $1,095) was gone.
Read the case – Navbharat TimesRefund Trap
A now-common scam: fraudsters “accidentally” send small payments, then ask the victim to send the money back. The UPI address link is fake.
Once they click it, the money vanishes – and there’s no dispute trail.
Explained – Razorpay
These scams don’t rely on user mistakes.
They rely on trust in the channel – SMS, UPI, or links that look just close enough.
And they pass quietly through the network unless something stops them before the click.
UPI fraud isn’t one thing – it’s a cluster of attack types, often delivered through SMS,
and most of them are painfully easy to execute.
Scams come in many flavors: a fake collect request, a cloned app, a QR code that sends instead of receives. Sometimes it’s a convincing call; sometimes it’s a single tap on a shortened link.
You don’t need to be careless. Just busy. Distracted.
That’s what these scams count on – and that’s what makes them work.
The thread tying them all together? A malicious link.
Often shortened, disguised, or redirected – waiting for a distracted click.
Most UPI Frauds rely on just one thing: a message that gets through.
A link in an SMS. A redirect in a shortened URL. A landing page that looks legitimate enough.
These scams don’t break the system — they use it as designed.
That’s where Fortress Firewall comes in.
Fortress operates at the messaging layer — scanning every message that flows through the network in real time. It looks beyond the text and into the link itself:
Where does it lead? Is it obfuscated? Has it been redirected? Is it hiding behind a shortener?
Fortress blocks scams before users can click them.
With powerful features like:
Real-time URL scanning with Atrinet URL Scanner and Google Web Risk.
Redirect chain detection to expose hidden destinations
Short-link expansion to neutralize obfuscation tactics
Machine Learning to detect evolving scam behavior
- Threat reputation feeds + heuristics to flag known fraud domains
Fortress doesn’t wait for complaints or content takedowns.
It acts before damage happens, at the only point where fraud can still be stopped: The Network.
Rid your network of UPI fraud now. Since most scams don’t need hacking. Just a click.
The real risk is in the last mile: phishing links, redirect chains, and silent fraud traffic that blends into traffic and gets ignored until it’s too late
And yes, much of it is still getting through your network.
Atrinet Fortress Firewall changes that.
It gives mobile operators and aggregators a real-time solution to block link-based fraud.
Fast, Accurate, and Invisible to the user.
If stopping fraud before the click matters, this is where you start.


























